
What I learned from a year of virtual and in-person events
Zoom CMO Kimberly Storin shares lessons from a year of virtual, hybrid, and in-person events—and why virtual experiences should stand on their own.
Practical steps to help protect your content and deliver a smooth, professional webinar experience.
Updated on September 09, 2025
Published on September 02, 2021


Webinars are a powerful way to connect with customers, employees, and partners. In 2024, Zoom hosted over 6 million events with 268 million participants. Some were public, some invite-only. Each one of them required proper security to run smoothly.
Disruptions in a public webinar can derail your message. Uninvited guests in a confidential session can expose sensitive information. Zoom Webinars and Events provide flexible controls so you can match security to your audience and content.
Here are 7 essential webinar security tips to help you deliver a safe and seamless experience.
Invite-only webinars often contain sensitive information, like company all-hands, closed supplier briefings, or major announcements. Here’s how to control access:
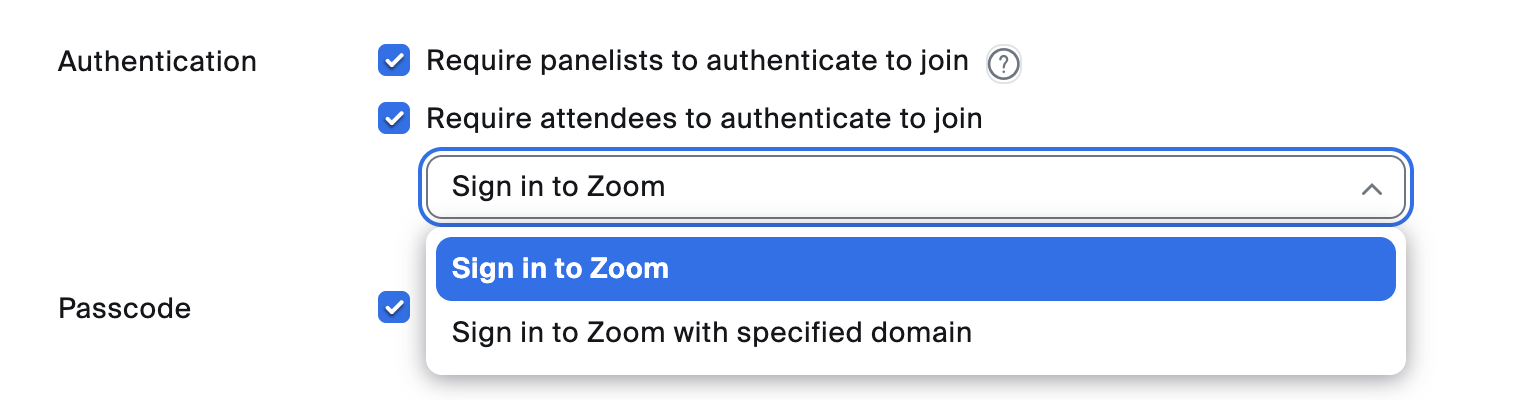
Authentication helps ensure only verified Zoom users can join. This is the MOST important safety measure to prevent uninvited guests.
When to use it: Employee-only sessions or trusted partners.
How it works: Admins can configure authentication profiles to require sign-in for attendees or panelists and it's strongly recommended to do it for both groups. They can also match email domains, or block specific domains.
Why it helps: Can help prevent uninvited participants from gaining access.
How to do it: When configuring your webinar, select "Require attendees to authenticate to join" and "Require panelists to authenticate to join."
Hosts can require a passcode for entry.
When to use it: Groups where you may not know every attendee but still want to limit access, such as a customer briefing restricted to people from a specific company.
Pro tip: Remind panelists not to share join links or passcodes outside the approved group. This setting is not recommended for especially sensitive content

When you add an image watermark, it can deter participants from sharing unauthorized screenshots or recordings.
How it works: Each participant sees their email address superimposed onto the shared content they are viewing.
Why it helps: Any screenshots or recordings made will include the participant's email address, thus identifying the source of any unauthorized content sharing.
Public webinars are usually designed for marketing, thought leadership, or community engagement. They’re open to anyone with the link, which makes them powerful but also more susceptible to disruptions.
Learn more about getting started with Zoom webinars and managing registration.
Chat can boost engagement or create distractions.
When to allow it: Marketing webinars where participants connect with your team or each other. Assign a moderator to manage chat and remove inappropriate messages.
When to disable it: Focused sessions where interaction isn’t critical. Panelists can still chat privately.
Q&A lets participants ask questions, but visibility should be managed.
Best practice: Disable the “Allow attendees to view” setting so participants only see questions chosen by hosts and panelists.
Pro tip: Have at least one extra member of your team dedicated to managing the Q&A.
If a disruption occurs, hosts can mute or remove panelists, promote attendees to panelists, or suspend all participant activity.
When to use it: If someone shares inappropriate content, quickly suspend activities, remove the participant, then resume the webinar. Make a brief announcement such as: “Thanks for your patience, we’ll continue in just a moment.”
Pro tip: For larger audiences (~70 attendees and above), have one or two colleagues manage the host controls in the background. This lets the moderator focus on the content and their voice-over.
No matter the audience, these steps are designed to protect your content and your attendees.
Before the event:
Review registration lists and remove suspicious entries.
Confirm security settings like authentication, passcodes, chat, and Q&A match your audience.
Remind panelists not to share their personal join links.
During the event:
Perform a quick pre-flight check minutes before going live.
Have a co-host or moderator focus on participants, chat, and Q&A.
Use “Suspend participant activities” if needed to regain control instantly.
Whether speaking to hundreds or thousands, Zoom Webinars gives you the tools to balance engagement with security. With the right settings, you can focus on your message while worrying less about disruptions.
For more resources, visit the Zoom Webinars Support Center and check out our guides in our Trust and Safety Center.